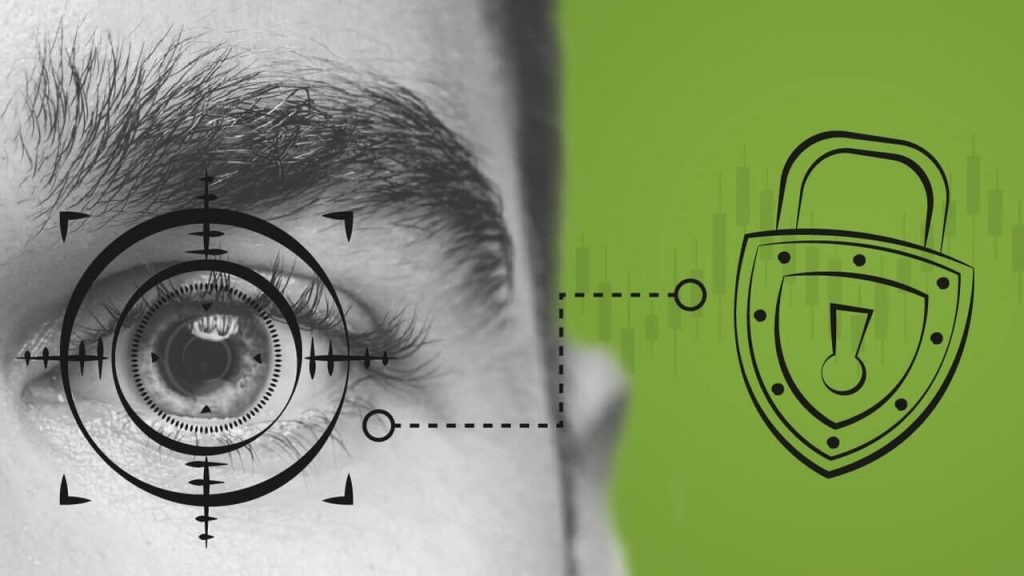
Since its first appearance in 1989, ransomware has evolved its method, generating more and more unfortunate victims. This type of malware infects your computer, demanding money to reset the operating system.
Therefore, technological security is essential to avoid cyberattacks that can steal your cryptocurrencies, but do you know how to do it?
It is about time that you block this malicious software and shield your assets. Stay tuned and discover the top ten tips to protect yourself wisely and practically below.
Let’s talk about Ransomware and how they operate in the crypto world
Do you know what ransomware is? It is a type of “malware” (an English term that comes from the union between the words “malicious software” or malicious software). They are designed to infiltrate the system without the consent of the user.
Malware can take several forms and one of them is Ransomware, known as computer data hijacking. The Anglo word “ransom” means “ransom” and is the target of this criminal system.
Generally, you require a key to unlock your computer, which is offered to you in exchange for the financial ransom. That is, after blocking access to the computer and encrypting files to make them inaccessible, a sum of money is requested.
This threat has caused damage to networks of large companies, hospitals, airports, even government agencies around the world. There are several ways to get victims using this method:
- Phishing: Very common and materialized in the form of links or links from emails, hidden as legitimate addresses. You can receive an attachment in your email and activate ransomware with just one click.
- Malvertising: Through false online advertising, they can access your information.
- Exploits: These are packages or kits with vulnerability codes, designed to exploit problems on applications or operating systems, spreading malware.
In the crypto universe, ransomware has also wreaked havoc, witnessing attacks globally by 200%. How do they operate?
They are becoming increasingly sophisticated, as an example in Singapore, taking advantage of the pandemic situation. Through crypto hijacking, cybercriminals take over devices to mine cryptocurrencies.
This attack increased by 300% during the first quarter of 2020. Another case is the use of email campaigns, announcing treatments for COVID-19.
They can also offer you crypto investments with a high return on profitability, which is attractive. However, you would be facing ransomware that will absorb your crypto assets in seconds. So, what to do?
It is essential to understand that you are not unprotected. You just have to be prudent and have advanced tools, as well as a professional and trained team.
It is important to have a robust, reliable platform equipped with technological security features. You will be able to exchange your cryptocurrencies in a safe environment, with timely support and ease of use.
How is Ransomware traded on the black market?
On the dark web, you can find countless offers for ransomware as a kind of legal service. From updates to technical support, including a well-known one, Ranion, has monthly or annual plans.
Malware is also offered free of charge, so that the client is in charge of spreading it through emails or spam, obtaining profits from the victims.
Is the use of Ransomware tools legally penalized?
These tools and software are available on the dark web. This indicates that they are not endorsed since they represent damage to any system, translated into millionaire losses.
The problem is that cyber attackers are in a state of anonymity behind their computers in hiding.
Avoid Ransomware Attacks With These Recommendations
Do you want to know how you can protect yourself safely? Here are some good tips.
Stay informed about threats that may affect your data
Information is key. From time to time, ransomware is updated, as well as technical measures to deal with criminals. Look for reliable sources that provide you with accurate information about these threats.
Secure your personal or company equipment with multi-factor authentication
Known as MFA, it is an element that verifies your identity through verification and authentication methods. The KYC is designed to offer you protection and shield your operation.
Perform your crypto assets operations from a desktop computer instead of your cell phone
On your desktop computer, you would be in a lower risk position than on your smartphone. The cell phone is more vulnerable to receiving ransomware and you do not have as many tools or power as a computer.
Make a regular backup of your data
When attacked by ransomware, you could lose valuable information. Protect yourself with an updated backup, so you can restore all documents from a backup.
Unlock the visibility of hidden files on your pc and look for irregular extensions to take corrective action
With Cryptolocker and Windows default settings, you can hide known file extensions. By unchecking certain boxes you can see the extension of each one and detect doubtful files.
Filter the search in your emails .EXE files
Configure your mail using filters to reject .exe extensions or you can convert them to ZIP with a password if you want to exchange executable files.
Find out and buy the Cryptolocker Prevention Kits
They are very useful to fortify you against ransomware. It disables executables from the TEMP directory and files from the APP DATA and LOCAL APP DATA folders.
Keep your desktop computer’s antivirus and software up-to-date
Minimize the risk by updating your software, computers with outdated systems are more prone to attacks. Also, you must have a powerful antivirus that has many advanced features.
Disconnect Wi-Fi or Ethernet immediately when opening a suspicious file
This way you can quickly cut communication with the C&C server before it finishes encrypting your data. It is not a guaranteed technique but it is well worth a try.

Hire a technical service specialist to clean your computer every so often
A professional has the solid knowledge to provide you with more security, making periodic reviews and eliminating suspicious files. Try to hire trained personnel, with a track record and ready to help you.
Conclusions
Ransomware affects millions of computers globally, stealing millions of dollars in cryptocurrencies. The solution is to follow these simple recommendations and put yourself in the hands of experts.
To buy, sell or simply exchange your cryptos, you must do it in a safe environment equipped with high technology. Do you know where to find it?

At CCOINS we offer you a multifunctional, intuitive, multilanguage, and easily accessible platform. This is how we protect you from fraud, guaranteeing you secure and agile transactions.